CSS Question Paper solution May 2023
Table of Contents
Duration: 3hrs [Max Marks:80]
1 a) Describe services and mechanisms. CSS
Answer : https://www.doubtly.in/q/describe-services-mechanisms-css/
1 b) ECB and CBC block cipher.
Electronic Code Book (ECB) –
Electronic code book is the easiest block cipher mode of functioning. It is easier because of direct encryption of each block of input plaintext and output is in form of blocks of encrypted ciphertext. Generally, if a message is larger than b bits in size, it can be broken down into a bunch of blocks and the procedure is repeated.
Procedure of ECB is illustrated below:
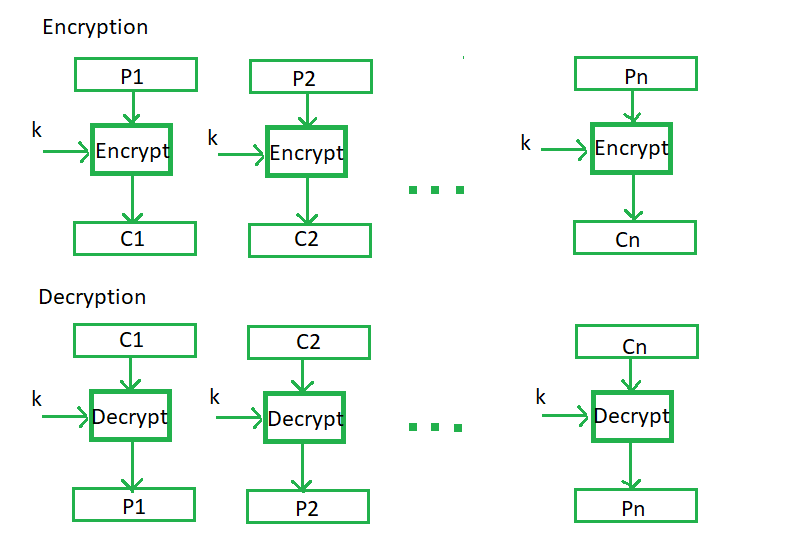
Advantages of using ECB –
- Parallel encryption of blocks of bits is possible, thus it is a faster way of encryption.
- Simple way of the block cipher.
Disadvantages of using ECB –
- Prone to cryptanalysis since there is a direct relationship between plaintext and ciphertext.
Cipher Block Chaining –
Cipher block chaining or CBC is an advancement made on ECB since ECB compromises some security requirements. In CBC, the previous cipher block is given as input to the next encryption algorithm after XOR with the original plaintext block. In a nutshell here, a cipher block is produced by encrypting an XOR output of the previous cipher block and present plaintext block.
The process is illustrated here:
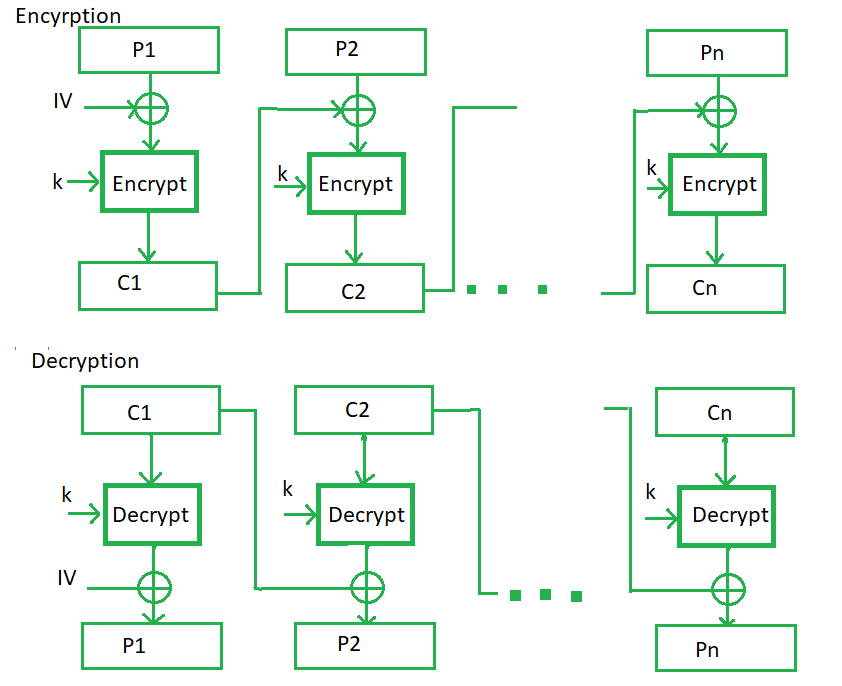
Advantages of CBC –
- CBC works well for input greater than b bits.
- CBC is a good authentication mechanism.
- Better resistive nature towards cryptanalysis than ECB.
Disadvantages of CBC –
- Parallel encryption is not possible since every encryption requires a previous cipher.
1 c ) Why digital signature and digital certificates are required?
Digital certificates and signatures are required to ensure the authenticity, integrity, and confidentiality of digital information and communications. In the digital world, it is essential to have a reliable way to identify users, verify their identities, and protect the data they transmit.
Digital certificates are used to verify the identity of the user or organization that holds the certificate. They contain identifying information, such as the user’s name and public key, and are issued by trusted third-party Certificate Authorities (CAs). When a user presents their digital certificate to another party, that party can verify the certificate’s authenticity and trust that the user is who they claim to be.
Digital signatures, on the other hand, are used to ensure the integrity of digital information. A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. It is generated using a private key that is only known to the signer and can be verified using the signer’s public key. By adding a digital signature to a document or message, the signer can prove that they created or approved the content, and that the content has not been tampered with since the signature was applied.
1 d ) What is keyed and keyless transposition ciphers ?
Transposition Cipher:
A transposition cipher does not substitute one symbol for another (as in substitution cipher), but changes the location of these symbols. It reorders (jumbles) the given plain-text to give the cipher-text. They are of two types: Keyed and Keyless Transposition Cipher.
Keyless Transposition Cipher:
In this cipher technique, the message is converted to ciphertext by either of two permutation techniques:
a. Text is written into a table column-by-column and is then transmitted row-by-row.
b. Text is written into a table row-by-row and is then transmitted column-by-column
The first method (a) is also popularly known as Rail-fence cipher
E.g. We need to send the message “DEFENDTHEEASTWALL”. Arranging into tables we get :
Now, the message is sent row-by-row. So Ciphertext is “DFNTEATALEEDHESWL”(Note: the no. of rows is 2 by default, unless specified)
Similarly for the (b) method, we can arrange the same above message into tables with four columns.
The Data is then transmitted column-by-column as “DNETLEDEWFTAAEHSL”
Keyed Transposition cipher:
In this approach, rather than permuting all the symbols together, we divide the entire plaintext into blocks of predetermined size and then permute each block independently.
Suppose A wants to send a message to B “WE HAVE AN ATTACK”. Both A and B agreed to had previously agreed oved the blocks size as 5. So the blocks would be as:
The last character X is a bogus character so as to complete the block size of 5.
A and B is using the following key for encryption and decryption:
1 e ) Explain clickjacking and session hijacking.
Answer : https://www.doubtly.in/q/explain-clickjacking-session-hijacking/
2 a ) Explain DES algorithm with reference to following points:
- 1. Block size and key size
- 2. Need of expansion permutation
- 3. Role of S-box
- 4. Possible attacks on DES
DES (Data Encryption Standard) is a symmetric block cipher that was widely used in the 1970s and 1980s. It uses a 64-bit block size and a 56-bit key size, which is considered relatively small by modern standards.
Block size and key size:
The block size of DES is 64 bits, which means that it can encrypt messages up to 64 bits in length. However, if a message is longer than 64 bits, it must be broken up into multiple 64-bit blocks and encrypted separately. The key size of DES is 56 bits, which means that there are 2^56 possible keys. However, due to weaknesses in the algorithm, the effective key size is only 48 bits.
Need for expansion permutation:
The expansion permutation is used to expand the 32-bit input of the Feistel function to a 48-bit value, which is then XORed with the round key. The purpose of the expansion permutation is to provide diffusion by increasing the number of bits that are affected by each round of the Feistel function. This helps to make the algorithm more resistant to cryptanalysis.
Role of S-boxes:
The S-boxes (Substitution boxes) are a key component of the DES algorithm. They take a 6-bit input and produce a 4-bit output, based on a fixed lookup table. The S-boxes provide confusion by making it difficult to determine the relationship between the input and output of the Feistel function. This helps to prevent attacks such as differential cryptanalysis.
Possible attacks on DES.
Brute-force attack: Since DES uses a relatively small key size of 56 bits, it is vulnerable to brute-force attacks. This involves trying every possible key until the correct one is found. While this may seem like an overwhelming task, advances in computing power have made it feasible to perform a brute-force attack on DES within a reasonable time frame.
Cryptanalysis attack: This attack involves analyzing the encryption algorithm to find vulnerabilities that can be exploited to decrypt the message. Cryptanalysis attacks can be targeted at the algorithm itself or at the implementation of the algorithm.
Side-channel attacks: These are attacks that exploit weaknesses in the implementation of the algorithm, rather than weaknesses in the algorithm itself. For example, an attacker could measure the power consumption of a device while it is running the DES algorithm to gain information about the key.
2 b ) Use the playfair cipher with the keyword “example” to encipher “The algorithm name is playfair cipher”
Detailed slution : https://www.doubtly.in/q/playfair-cipher/
3 a ) What are properties of hash function? Compare MD-5 and SHA hash algorithm.
the properties of a hash function
- Deterministic: For the same input, a hash function must always produce the same output. This property ensures consistency and reliability in hash computations.
- Fast Computation: Hash functions should be computationally efficient, allowing for quick computation of hash values even for large inputs. This property enables hash functions to be widely applicable in various applications without significant performance overhead.
- Pre-image Resistance: Given a hash value, it should be computationally infeasible to find any input that produces that hash value. In other words, it should be difficult to reverse the hash function and recover the original input from its hash value.
- Second Pre-image Resistance: Given an input, it should be computationally infeasible to find another input that produces the same hash value. This property ensures that given one input, it is difficult to find another input with the same hash value.
- Collision Resistance: It should be computationally infeasible to find any two distinct inputs that produce the same hash value. This property ensures that it is difficult to find collisions, where two different inputs produce the same hash value.
- Avalanche Effect: A small change in the input should produce a significantly different output. In other words, even a minor change in the input should result in a completely different hash value. This property ensures that similar inputs produce very different hash values, enhancing security.
