Introduction
TCP Three-Way Handshake known as Transmission Control Protocol (TCP). This protocol is the unsung hero behind the scenes, ensuring that your emails, videos, and web pages travel from one end of the world to the other intact and in the right order. At the heart of TCP lies a fundamental process called the “Three-Way Handshake,” a choreographed introduction that allows devices to establish a connection before exchanging data. In this article, we’ll unravel the mysteries of this handshake, exploring its significance, inner workings, and everyday analogies to make it all crystal clear.
Table of Contents
What is TCP?
Before diving into the Three-Way Handshake, let’s briefly understand what TCP is and why it’s crucial. Transmission Control Protocol, or TCP, is one of the core protocols that powers the internet. It’s responsible for reliable, error-checked data transmission, ensuring that the information you send or receive reaches its destination accurately. Imagine it as a postman who not only delivers your letters but also ensures they arrive in the correct order and without coffee stains.
What is the TCP Three-Way Handshake ?
The Three-Way Handshake is like a secret handshake for devices on the internet. When two devices, such as your computer and a website’s server, want to talk to each other, they don’t just start chatting right away. Instead, they follow a structured dance with three steps to make sure they’re both ready and willing to communicate.
Detailed Explanation of the Three-Way Handshake
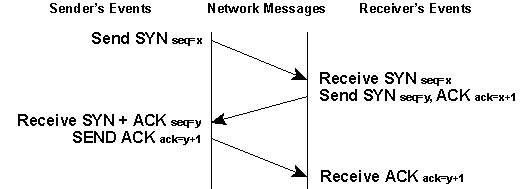
Step 1: SYN – Client initiates the connection Imagine you’re at a party, and you want to strike up a conversation with someone. You walk over and say, “Hi, I’d like to talk.” In the world of TCP, this is the client’s way of initiating the connection. The client sends a packet with a special flag called SYN (Synchronize) set to 1. It’s like saying, “Let’s talk, and by the way, here’s a number to help us keep track of our chat, let’s call it our ‘sequence number.'”
Step 2: SYN-ACK – Server responds to the client Now, imagine the person you approached at the party responds positively and says, “Sure, I’d like to chat too.” In the TCP world, this is the server’s response. The server sends a packet with SYN (synchronize) set to 1 and ACK (acknowledgment) set to 1. This packet says, “I’m ready to chat, and here’s my ‘sequence number,’ plus, I see your ‘sequence number,’ so let’s use it for our conversation. I’m ready!”
Step 3: ACK – Client confirms the connection In our party analogy, this is like you saying, “Great, let’s talk!” The client sends another packet with the ACK (acknowledgment) flag set to 1. This packet confirms the server’s readiness and acknowledges the server’s “sequence number.” Both sides now have a shared understanding, and they’re ready to have a conversation. The connection is established!
Simply Friendly Explanation
To make this concept even simpler, think of the Three-Way Handshake as a greeting before a meaningful conversation. It’s like saying “Hello” and making sure the other person says “Hello” back before you start discussing important stuff.
Security and the Three-Way Handshake
While the Three-Way Handshake primarily serves to establish a connection and ensure data reliability, it also plays a significant role in network security. In an age where cyber threats and attacks are prevalent, the handshake process contributes to safeguarding your online interactions.
- Authentication: During the Three-Way Handshake, each side must confirm the other’s readiness and exchange sequence numbers. This serves as a basic form of authentication. It ensures that the communication partner is legitimate and not a malicious entity attempting to disrupt the conversation.
- Protection Against Spoofing: The sequence numbers exchanged in the handshake help in preventing spoofing attacks. It becomes extremely difficult for an attacker to impersonate a legitimate party when they lack the correct sequence numbers. This adds an extra layer of security to your online interactions.
- Data Integrity: By confirming the readiness of both parties before data transmission, the Three-Way Handshake helps in preserving data integrity. This process prevents unauthorized data injection and ensures that the information you send or receive remains untampered with during transit.
- Firewall and Intrusion Detection: Security systems and firewalls often inspect the Three-Way Handshake as part of their intrusion detection procedures. Anomalies or irregularities in this process can trigger alerts, enabling the detection and prevention of potential threats.
Uses, Needs, Pros, and Cons
Uses: The Three-Way Handshake is used to establish a reliable connection before data transmission. It ensures that both sides are ready to communicate and sets up a system for tracking the data exchanged.
Needs: This process is necessary for the internet to work correctly because it confirms that both parties are available to talk and sets up the rules for their conversation.
Pros: The Three-Way Handshake guarantees reliable data transmission, minimizing errors and data loss. It plays a critical role in ensuring the integrity of the information shared on the internet.
Cons: While the Three-Way Handshake is essential for reliable communication, it adds a small amount of overhead to the connection process. In some cases, this extra step can introduce a slight delay.
Conclusion
The TCP Three-Way Handshake may seem like a technical intricacy, but it’s the unsung hero that ensures the smooth, reliable flow of data on the internet. By understanding this process, you gain insight into the foundational principles that make the digital world a connected and efficient place. So, the next time you browse a website, send an email, or stream a video, remember that behind the scenes, there’s a Three-Way Handshake ensuring the conversation starts on the right foot. It’s the “Hello” of the internet, making sure everyone is ready to talk and keeping your online interactions secure and reliable.
references :
